-
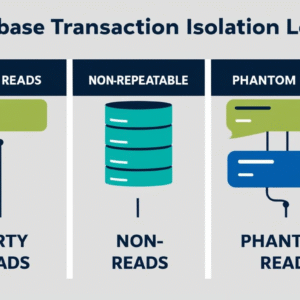
Database Transaction Isolation Levels: Dirty, Non-repeatable & Phantom Reads
Database transaction isolation levels are a critical aspect of building reliable backend systems. When multiple transactions execute simultaneously, several anomalies can emerge that threaten data integrity. These anomalies—dirty reads, non-repeatable reads, and phantom…
-
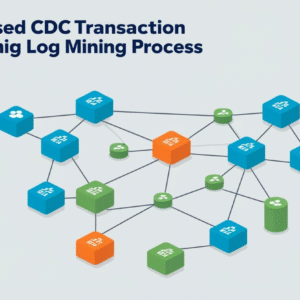
Log-Based CDC Transaction Log Mining
Log-based CDC transaction log mining enables real-time data replication without intrusive polling. It reads a database’s write-ahead log or transaction log to capture changes at source. Consequently, engineers avoid table scans and guarantee…
-
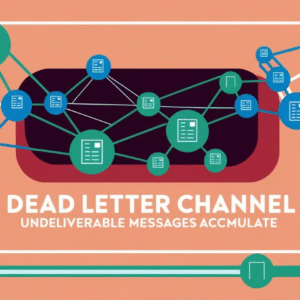
Dead Letter Channel: Handling Undeliverable Messages
Reliable message delivery is fundamental in distributed backend systems. However, not all messages succeed on the first attempt. Network issues, malformed payloads, or downstream service errors may prevent successful processing. Unhandled failures risk…
-
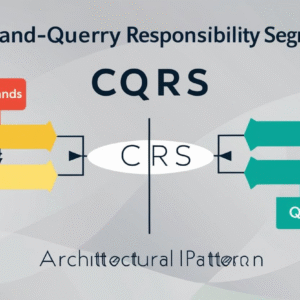
Command-Query Responsibility Segregation (CQRS):
Command-Query Responsibility Segregation (CQRS) is a design pattern in software architecture that separates read and write operations into different models. This post will delve into the technical aspects of CQRS and its implementation…